Steps to Reduce Your Cyber Security Risks
Wayne Robinson, Financial Planner at Modern Wealth Management, discusses the complex world of cybersecurity. He’ll cover some ways that you can eliminate up to 85% of your cybersecurity risks. The purpose of this webinar is to show you steps to reduce your cyber security risks and prevent yourself from being low-hanging fruit for nefarious online predators.
Complimentary Consultation Share this Video
Resources Mentioned:
- Resource Guide
- Update Protocol
- Personalized Purpose-Focused Digital Protection Plan
- The Guided Retirement Show Cyber Security episode:
If you have questions about Cyber Security, we can help. Give us a call at 913-393-1000 or schedule a complimentary consultation below to get started today.
Video Transcript
Hi, everybody. Thank you so much for attending the cyber security workshop. The content, as you all know, will forever be changing. So we’re going to try to keep it as current as we can for you.
There’s a lot of information, there’s a lot of action steps to take, but there’s a lot of support material that will come in conjunction with this workshop, which you can find in the resources section above.
If there are things in here that you miss or worry you’ve missed something, don’t worry; everything we discuss is available in the resource section.
Steps to Reduce Cyber Security Risks

We are going to cover several steps. Don’t worry; they are going to be fairly easy. I say fairly easy because it will be elementary for some folks, and for others, it might be more challenging, but we can work through this together.
Marc Goodman’s “Future Crimes”

The inspiration behind this workshop was Marc Goodman. He wrote the book Future Crimes.
We saw him at the TD Ameritrade conference, and his speech was so impactful, so powerful that we took it to heart. He said, “As financial professionals, we owe it to our clients to try and help protect them in this arena.” And it just gets worse and worse. The cyberattacks will elevate; they’ll get more prevalent. So we want to do all we can to help you protect yourselves.
Future Crimes
In this book that he wrote, Future Crimes, there are some incredible stories. He starts this book with the opening from The Matrix. For those of you that haven’t seen The Matrix, it’s a futuristic movie, and he offers the red pill, which you wake up oblivious to everything that goes on, and ignorance will be blissful. Or you can take the blue pill, and it will open your eyes to the reality of the situation, and your life will forever be different.
So he says, “Continue reading or don’t read, take the red pill, wake up ignorant and blissful, take the blue pill, we’ll see how far down the rabbit hole this goes. I had bought the books so obviously you know which pill I took. I took the blue pill, and I was a nervous wreck as I read this book, as everyone in this office will attest to.
But some of the stories in the book are cool. One account is about Stuxnet, which disrupted Iran’s nuclear program with a little worm embedded into their computer systems.
They just played that everything was fine for years, but behind the scenes, that worm masked the destruction of nuclear reactors. It was quite something.
So it can be used for good, and it can be used for evil. But he is the inspiration. It’s his protocol. I would encourage everyone to go to his site, buy his book, read his book. He is an expert in this field.
A Quick Story About Marc Goodman
Quick story about Marc, then we’ll get into the content. He was a detective for the Los Angeles Police Force. And back in the early 80s, his captain came and said to him, “Marc, do you know how to spell-check in Word?” And he said, “Yes, I do.” He said, “Perfect. You’re going to head up cyber security.” That was the criteria for getting that job in the early 80s. That was very, very funny. He ended up working with FBI Interpol, so he’s definitely a good source for this information.
If It Can Happen to Him, It Can Happen to You

Mat Honan, who was an editor for Wired magazine, a young guy in the industry. If anybody were not going to get hacked, it would be Mat Honan. But the reason I bring this story up is if it can happen to him, it can happen to any one of us. So don’t feel bad, but let’s protect ourselves from it.
His entire digital world was wiped out by a 14-year-old hacker that wanted his Twitter handle was @Mat. I mean, he obviously had his eyes opened to the fact that it can happen to anybody.
Goal: Reduce Your Risk by 85%
Today’s goal is to follow these steps that we’ll discuss today. We’re hoping you’ll reduce your cyber security risk by 85%. There’s no bulletproof solution as this is ever-changing, and the criminals are getting better and more prominent, and there’s obviously a market for this.
What we want to help you accomplish today is take you out of range, right? Criminals love to target low-hanging fruit. They like the ease of crime. If we can get you higher and higher up into that tree, where we bring you out of reach, that’s like that saying, as long as you can outrun your slowest buddy, the bear will eat him. Right? That’s the goal. We want to get you out of reach.
The Biggest Lie About Cyber Security

The biggest lie is that I have nothing to hide, right? The truth is we all have something to hide. Most of us take our phones into private places. Yeah. That itself is enough reason to have something to hide. But we certainly do. And the myths that this is complicated can put that to bed just like we can dieting.
There are millions and millions of diet books out there, and as Mark will say, “They all have the same message. Right? Eat less, move more.” Cyber security doesn’t have to be any more complicated than that. With some simple steps and we can help protect you.
It is Time…to Update!

So the first step is to update. It is time. Definitely, it is time. Simply updating and getting patches on our computers and our phones will significantly impact protecting us.
Global Threat Intelligence Report

NTT Security did this study, and they studied six billion cyber attacks. Interestingly, 76% of the six billion people, 76% of them had outdated software by two years. This means that simply by updating their software, 76% of those attacks could have been avoided. Right?
When You See this, Act!
So I know that a lot of times now, it’s automated; we can choose to have automatic updates. If you haven’t chosen to do it automatically, then do it. Many of these companies are making it so that it’s easy to get our patches, but that’s hugely important. So turn that on.
We’ll also have a reoccurring theme in this workshop that talks about how most attacks are psychological, not technological. Even though we are led to believe it’s a technical issue, more often than not, it’s psychological. They want to bait us right into thinking that.
Passwords Matter: The “Gateway”
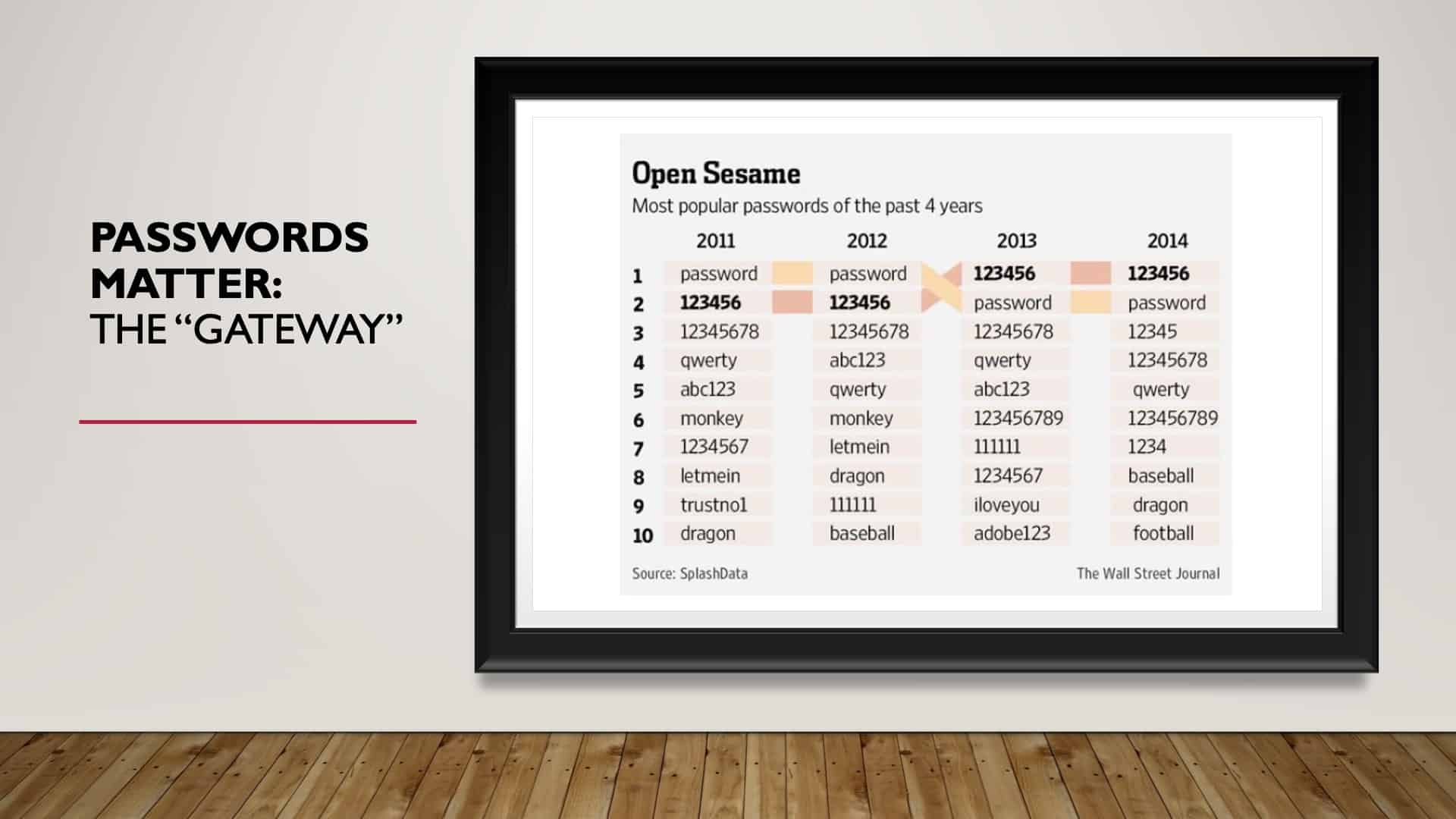
Step number two, passwords. Passwords are the gateway. They are the key. They let people into our world, right? So our password is critical. But as you can see, back in 2011, when the internet was just a baby, and we were just getting warmed up, the most common password was ‘password.’ In 2012, as we learned to become more secure, the number one password in 2012 was ‘password.’
You guessed it. However, there was promise because, in 2013, we learned. The number one password was ‘123456.’ The second most used password was ‘password.’ ’14, nothing changed.

In 2015, nothing changed.
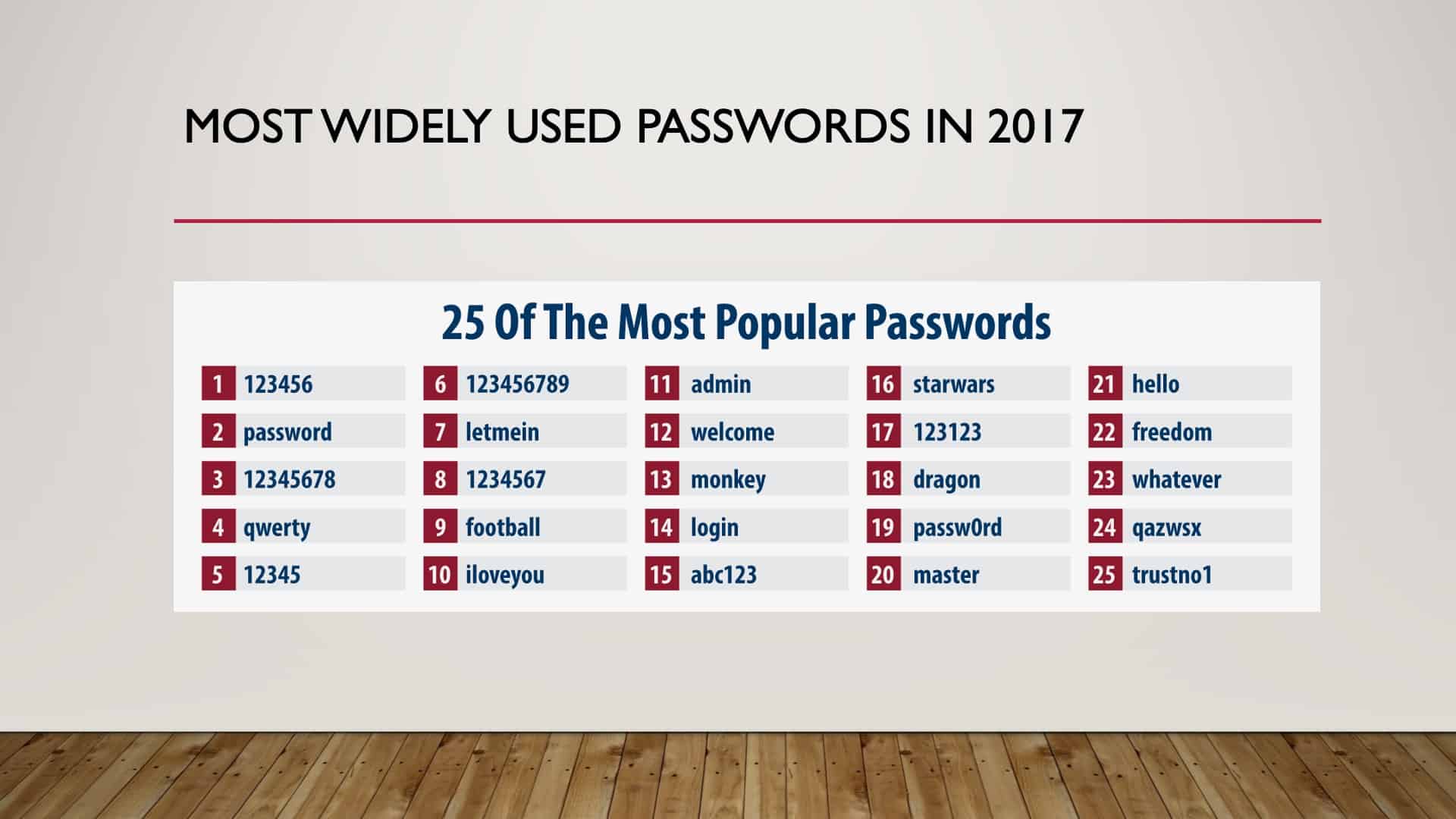
I even skipped ’16. I went straight to ’17 because you’re getting a reoccurring theme here, right? ’17, nothing has changed. The most popular password, ‘123456’, and the second most popular password, still, ‘password.’
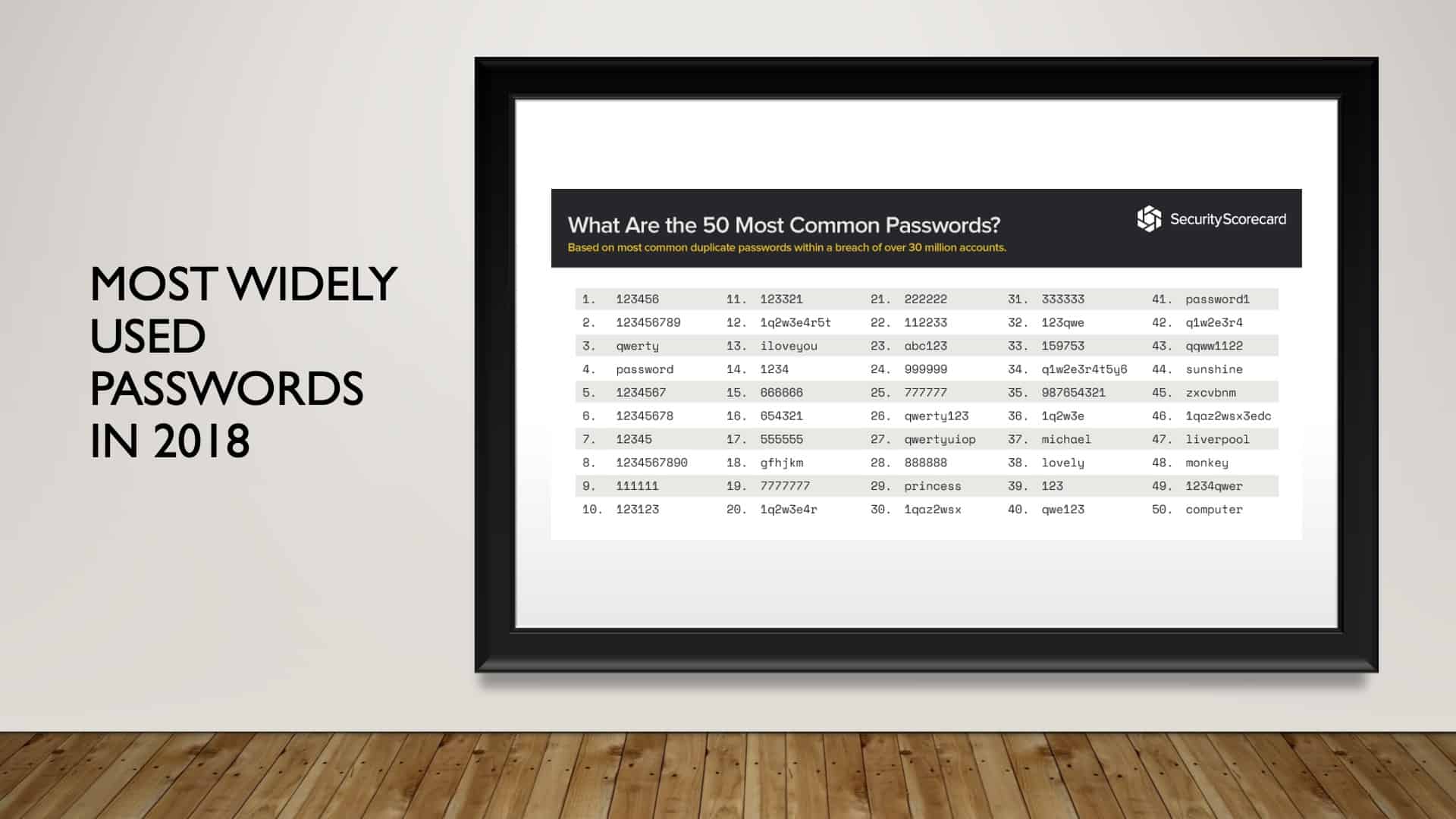
Let’s jump to ’18. We have ‘password’ moved down to the number four spot, but ‘123456’ was still number one.

And then in ’19, we have 23.2 million users still using ‘123456.’ Password is down to number four.
Creating a Safe Password
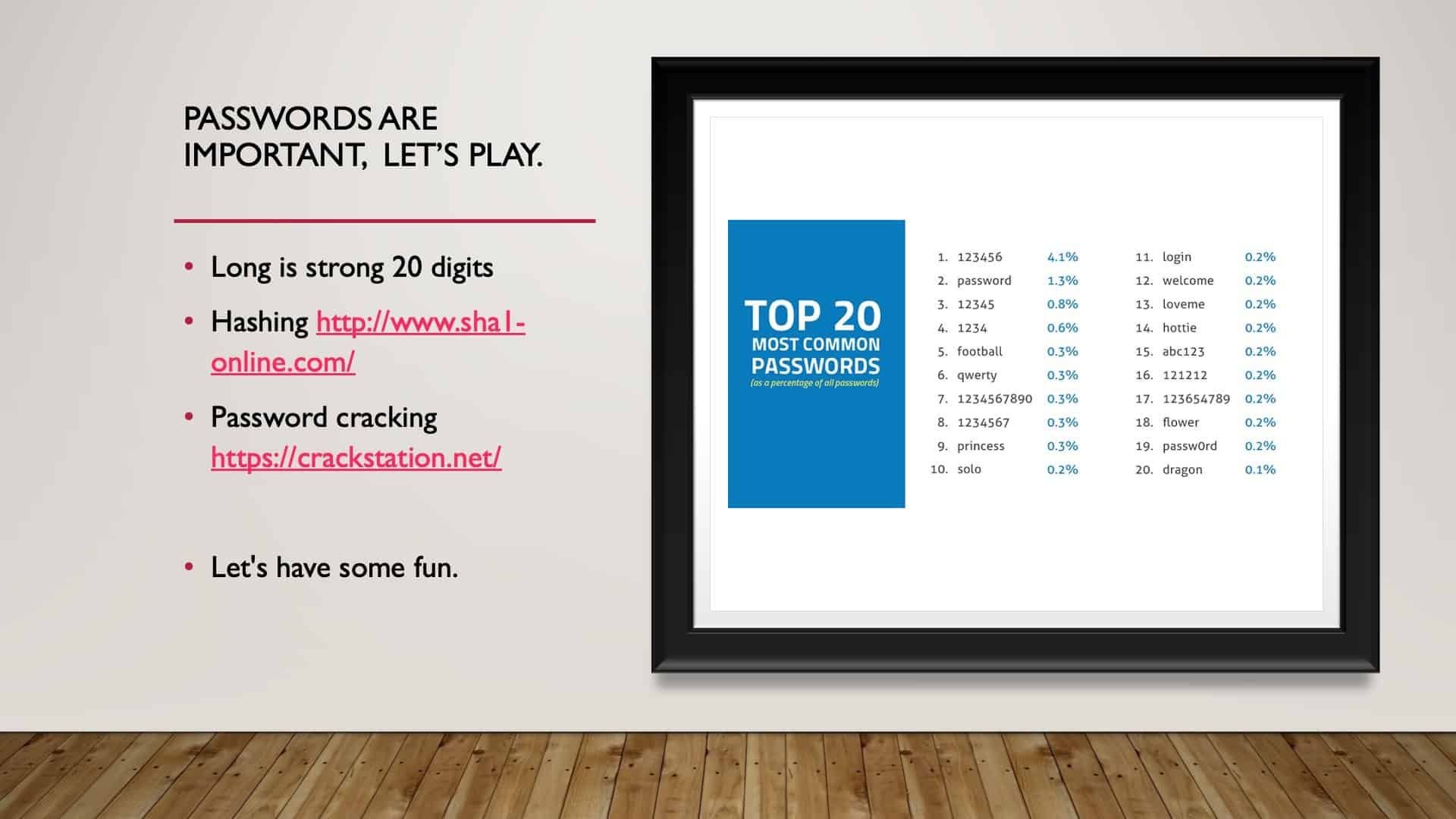
Note: For this section, we suggest watching the video from the minute mark 8:26 to 14:25.
We are going to do now a quick hands-on example of how to get a safe password. Okay, so on the screen, what you see here is an encryption tool. This is to encrypt plaintext, right? And what we have here is called hashing encryption. And these all are different types of encryption.
Types of Encryption
So the one that I’m going to use here is I’m going to use SHA256, a later version of the SHA1, which was SHA, so it was solid back when it was created. And then it got to be crackable. So this is a more advanced version.
Hashing a Password
It’s going to take this password and remember, this is a very widely used password, so I’m going to use it, and I’m going to hash it. So what you’ll see is that the clear text will be transformed into just jibber-jabber, right? Digits and numbers that would be meaningless to the naked eye.
If you looked at that green stretch of numbers and letters, it would be meaningless. And that’s the whole design of encryption, which is to take something that’s plaintext, encrypted, so it makes no sense. So if someone hacks it, they just see that. Okay?
So we’re going to copy this whole set of digits and numbers, and we’re going to paste it into this crack station. This crack station is a free tool. So I would bet you that criminals have something a little bit more advanced, but I want to show you how this works for this illustration.
We’re going to tell if it isn’t a robot. And then we have to pick statues. Statue, statue, and statue, verify. Now what it will do is it will see if it can be correct. Okay? So within a split second, this complete encrypted hash of the word password was cracked instantaneously. Okay? So that’s not a safe one.
Enhancing the Complexity of the Password
Let’s start to now enhance the password to see what it will take to make it safe. So the first thing we do is capitalize, right? So if we capitalize password, that’s the first thing, put a capital letter in. Now I’ve hashed this. I’m going to copy it and paste it into that hashing tool, that cracking tool. So I’m not a robot, and we see if we can break it.
All right. So as you can see, there’s the capital P, it’s good, but it’s not enough. What happens if we change one of the letters to a digit? So let’s say P@ssword, right? We know that that now is the third step. So we hash that. We copy it. We see if the crack station can crack it. All right. Hopefully, you guys are finding this helpful. But let’s see just as a matter of interest if we can crack it. And boom, there it is. Everybody sees this right here. Okay. So this is good, but not good enough.
Let’s Make the Password Even More Complex
So let’s try one more thing, and let’s see if we put a number in there. So let’s change that to a zero. I’ve got P@ssw0rd with a number and a @ emblem. All right. So let’s hash it, bump, there it is encrypted. We copy it, paste it into the tool, go through the security. There we go. And we crack it. All right. Instantaneously, that encryption is correct. There it is, P@ssw0rd.
So I’m going to show you one more. And I hope that this last example doesn’t allow us to crack it. We’re going to break this word up. We’re going to say, Pass, another @ emblem, a word with a number in there. Okay? So let’s see, because this is not a non-dictionary word. We’ll see if we have solved this riddle. Okay. Everybody breathe a sigh of relief. We have cracked the cracking station. So you can see it was not found, right?
A Quick Reminder
Just as a reminder, as we go back to that password exercise, we see that we’ve taken the most popular password in history, and we’ve solved the riddle. We’ve made this cracking station not crack it by purely breaking the word up with an emblem, putting in a symbol, a capital, and a number.
I’m not suggesting that this is safe because, as I said, this cracking station is a free tool designed just to crack the hash. And I want to show you one last thing too.
If I change this to SHA512 and I hash it, you’ll see that it is significantly longer. Can everybody see that? It even runs off the page. That just shows you how, as we advance with cybersecurity, how things have to get longer and more secure and more complicated because criminals are keeping up, and we have to stay ahead of this as best we can. So that is SHA512, 512 indicating a lot more complexity, a lot more digits. Okay?
Password Manager
That was fun. The suggestion now, as far as the length of a password, what I’m about to say may scare a lot of you, is a minimum of 20 digits. Including all of those complex characteristics built into the numbers, digits, capitals, not words. Impossible to remember.
So a resource that might be useful is something that Marc Goodman suggests using, is Dashlane recommends. I personally use it.
What happens is you have a password that you create. Don’t lose that, don’t tell anybody what that is, and make it complex, but make it something you can remember.
Then Dashlane will automatically create passwords, complicated passwords automatically for all of your different sites. So if you log in to Dashlane, it’s remembered all of your passwords, and it automatically logs you into your various accounts with a very complex password.
If it gets hacked and one of your passwords becomes compromised, it will notify you, and it will automatically ask that you change that password. So it’s a very, very, very good, beneficial tool. This is in the resource guide.
WiFi Routers, Oh Boy!

WiFi routers are a gateway, again, into your world. Many old WiFi routers would come with a default password admin or something straightforward that would be expected of you to change your password for security.
If no one told you that, maybe you’re none the wiser. However, this is hugely important that you change the password. And if the router has software that needs to be updated, update the software.
Update Your Routers!
I found this article from PCMag go over as an example because NETGEAR routers owners are being warned that there are a couple of vulnerabilities. Seventy-nine models of NETGEAR routers, going back to 2007, have been affected. So, I suggest that if you have a NETGEAR router to get firmware updates so that your router is not susceptible to an attack. Okay. All right. So that’s very, very important.
A Strong Password is Not Enough

A strong password might not be enough on its own, so we encourage two-step verification authentication.
Two-Step Authentication
I know it can be painful and annoying, but if we can understand that it makes it so much more difficult to be hacked, it’s worth it. It’s just something that we’ve got to learn to embrace, and we love the two-step authentication, whether it be fingerprint or a token, anything like that.
Many of our devices allow for it, and many of our banks have adopted it because it’s good. I encourage you to do it.
Two-Step Authentication Resources
If you have no idea how to do it, another resource in the resource guide you’ll get is two-factor authentication that’s turnon2fa.com or twofactorauth.org. These are two sites that will help walk you through how to set up two-factor authentication on your own devices.
Be Careful What You Download
Another step that we need to be cautious of is being aware of what we download. Just because it’s in the app store or at Google Play, it does not necessarily mean that it is safe. Fortunately, both Apple and Google are monitoring to ensure that there’s nothing bad out there, but it doesn’t mean that they get it right all the time.
Google Chrome Extension Example
So here’s an example. Google has prevented 111 harmful Chrome extensions from running on its browser, 79 of which have been available from its Chrome store. So they’ve kicked 111 out of the Chrome store; 79 were available in the Chrome Store. They are malicious.
Unfortunately, those extensions were downloaded 32 million times through the Chrome store. 32 million downloads. Yeah. That’s not good. So how do we identify bad apps?
If there were an easy way, I would tell you, but if it’s new and hasn’t been rated, it might be a bit of a red flag. If it smells bad, it probably is bad. Just be aware, maybe do a little research, look at the reviews, perhaps look at what people are saying if it’s helpful. Be very, very careful of what you download.
Flashlight App Example
So an example of a free download. The flashlight for your phone, right? Everybody wants one because I need a flashlight for my phone. They’re handy tools.
But what I’m going to show you is an article that talks about the ten best free flashlight apps for your phone and the permissions that these apps ask of you to give them when you download this free flashlight app.
So the ten best Android flashlight apps with the least permissions and no malware. This is good news because there’s no malware found in these ten best Android flashlight apps.
However, they do ask for specific permissions.
Flashlight App Permissions
Number one, the Flashlight by SimGears; it’s asking to be able to take pictures and videos, control vibrations, control your flashlight, full network access.
Number two: the Color flashlight, take pictures and videos, view network connections, full network access. So we keep going.
Number three: the Tiny flashlight, take pictures, videos, run its start-up, prevent the device from sleeping, control vibrations, full network access.
Number four: take photos, videos, read battery statistics, full network access, view network connections. So you get the idea.
I’ll go down to number six, take pictures, videos, read home setting shortcuts, write home settings and shortcuts, view network connections, full network access, disable your screen lock, prevent the device from sleeping, install shortcuts, uninstall shortcuts. Right?
You get the gist of it. So this is free and we just happily say accept the terms, and the next thing you know, we’ve given up control of that device. So I want everyone just to be aware that sometimes, you know what? We have to be cautious, proceed with caution.
Okay. So just an example, right? Everybody has one. So I wanted to use something that everyone’s familiar with.
Very Alarming
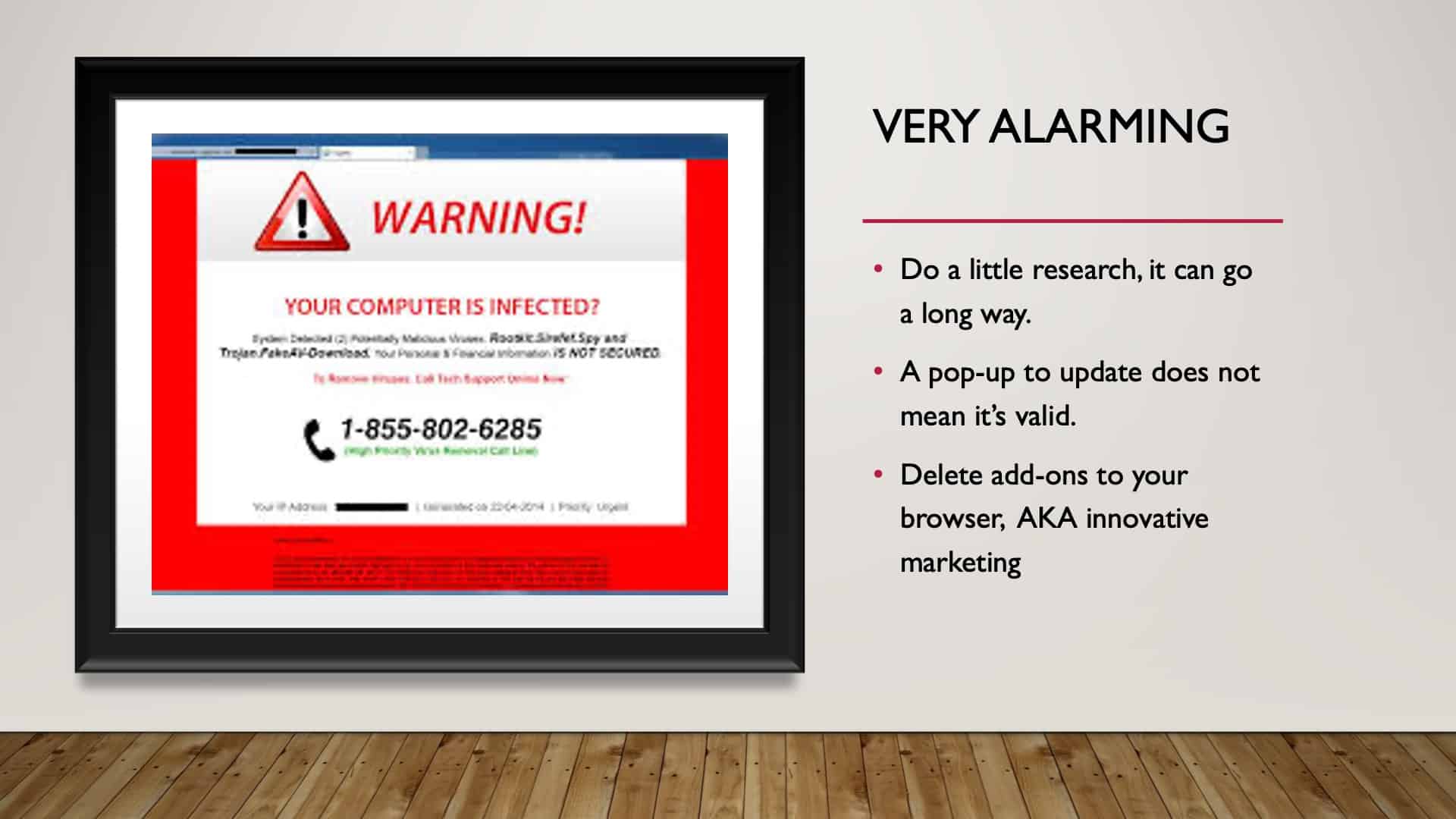
Going back to it might not be technological; it might be psychological. We get warnings that pop up on our computer warning your computer has been infected, and then in many cases, at least from my experience.
You might be experiencing something completely different; these have seemed to slow down for me. It’s not as frequent as it used to be. But again, I work primarily on my work computer here that has a lot of protective measures already built into it.
But if you’re working from home and getting these, it’s alarming because it takes one click in something that might not be genuine to install malware. So do a little research. Yeah. Call the provider, if it’s Mac, call Apple, just say, “Is this a genuine infection or not?”
Story from “Future Crimes”
There was a story in Marc’s book about Innovative Marketing, the company listed on the slide. They were an anti-malware company. At one point, they were up to $500 million in revenue a year. So very successful.
This company was embedding malware into the anti-malware so that at some point, you got a blue screen update and this very annoying alarm command to say, “You’ve been infected, call us.”
You call them, and they upsold you on some more of their product. They did get busted, thank goodness. The two founders are still at large, vanished. But so that you know, just because it says it doesn’t necessarily mean that it’s real.
Administrator Accounts

If you have one account on your computer by default and it’s your computer, you’re the administrator. You went into Best Buy, bought your computer, and if there is one account, you’re the administrator. You have the right to do anything you want on your computer, including installing software, deleting software, doing whatever you want.
If you get hacked, and you’re operating in the administration account, that means that the criminal who attacked you has the same rights as you.
Using a Standard User Account for Normal Use
It’s very important that you operate on a standard user account when you’re out in the big world of the internet. Create a standard user, a second account for your worldwide web surfing as a standard user.
The pushback that we might get is, “Well, all of my favorites, everything that I do, I don’t want to lose that, I don’t want to start over again.” So what you can do is create a standard account, then go back to your administrator account, right? Turn that into the standard account and then create the administrator account as the new standard account to use.
So flip-flop them, right? So that all of your bookmarks, everything is standard user, and it’s all there for you. And the one that has nothing saved is now the administrator. And you can get into that account to install software whenever you want. Okay? Hopefully, that all makes sense to you.
Study According to Microsoft on Admin Accounts

Microsoft did a study that just by not going out into the big, scary internet world as an administrator can mitigate 97% of your Windows vulnerabilities and 99.5% of Windows Explorer vulnerabilities.
With results like that, it makes perfect sense not to be out there as an administrator.
How Do You Know if You’re the Administrator?
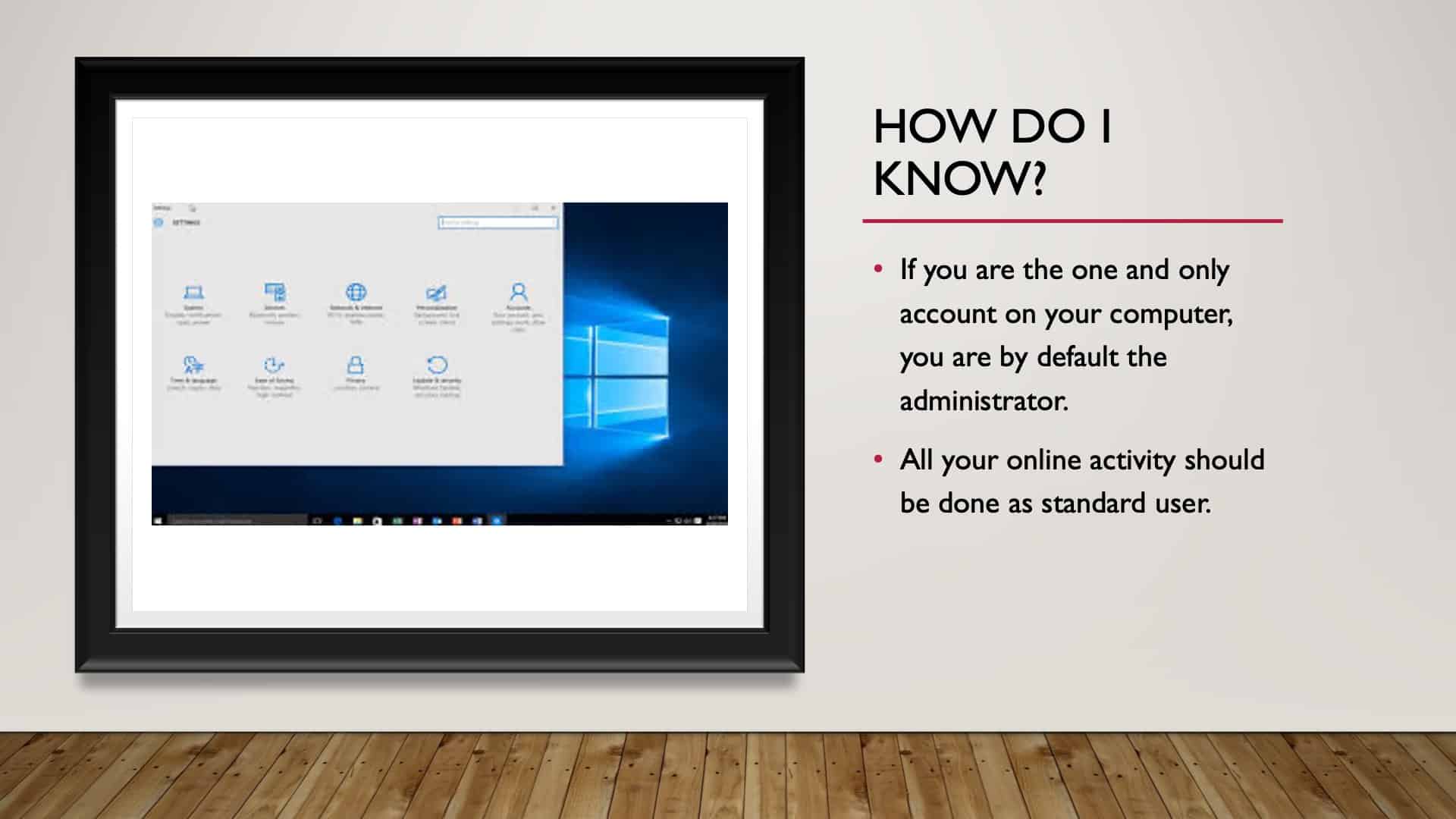
Again, hitting this point hard, go to your settings, go to accounts, see how many accounts you have.
If there’s one account by default, you’re the administrator, and if there’s more than one account, then one will be a standard account, one of them will be an administrative account. And you certainly don’t want to be out there as the administrator. Okay? Hopefully, that all makes sense.
The Psychology of Cyber Security
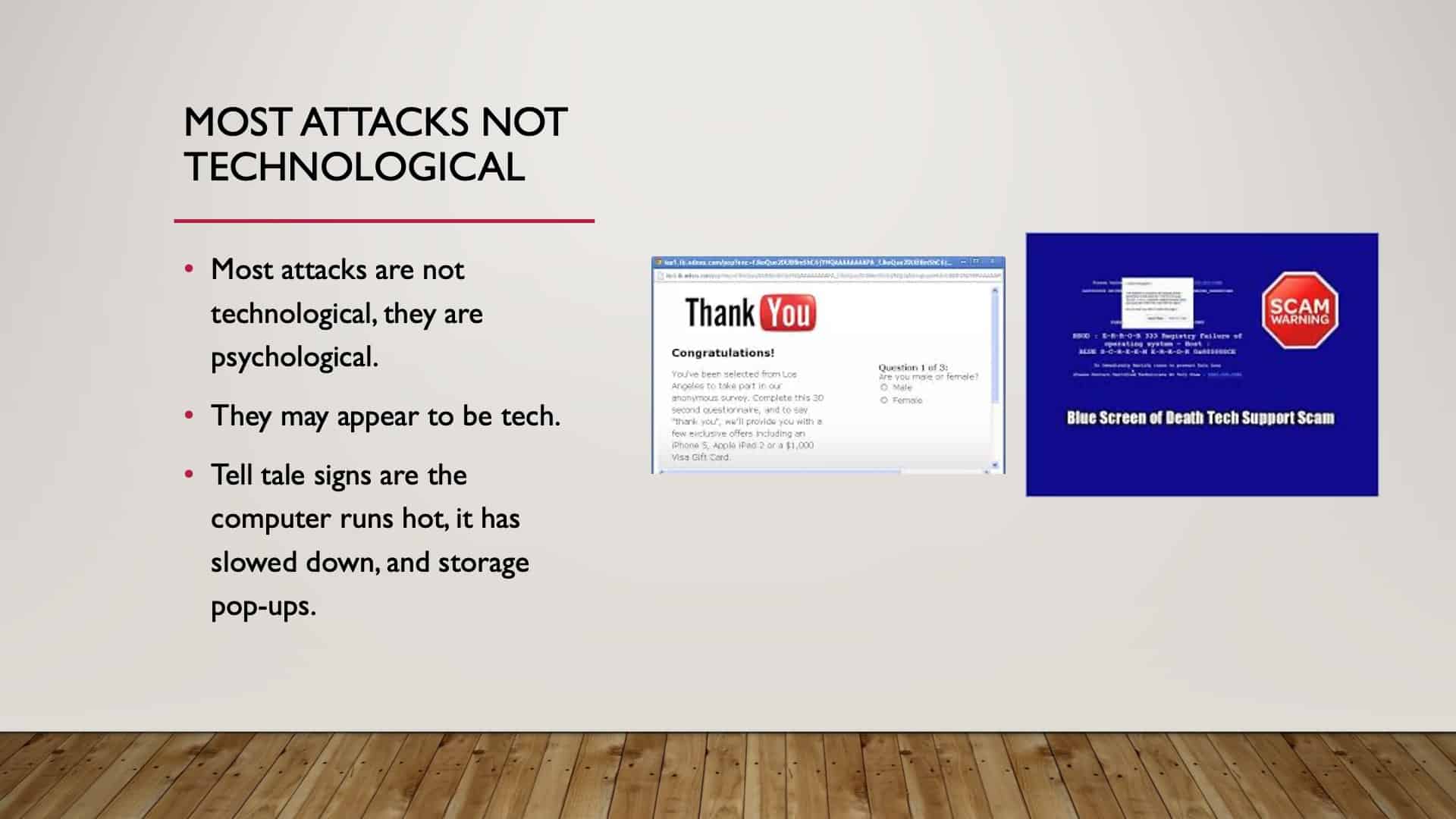
Most attacks are not just technological, even though we’re led to believe that they are. Again, just hitting this point, just because you get a warning doesn’t mean it’s true. Just take a moment of pause and think about it and then verify. Pause and verify.
Most attacks are not technological. Again, they are psychological. If your computer runs all the time, even when you’re not on it, the fan’s clicking on, it might be a sign that you are infected. If it runs slow, if you’re getting a lot of popups occurring, it might be a good indication that your computer has been violated.
Turn Off
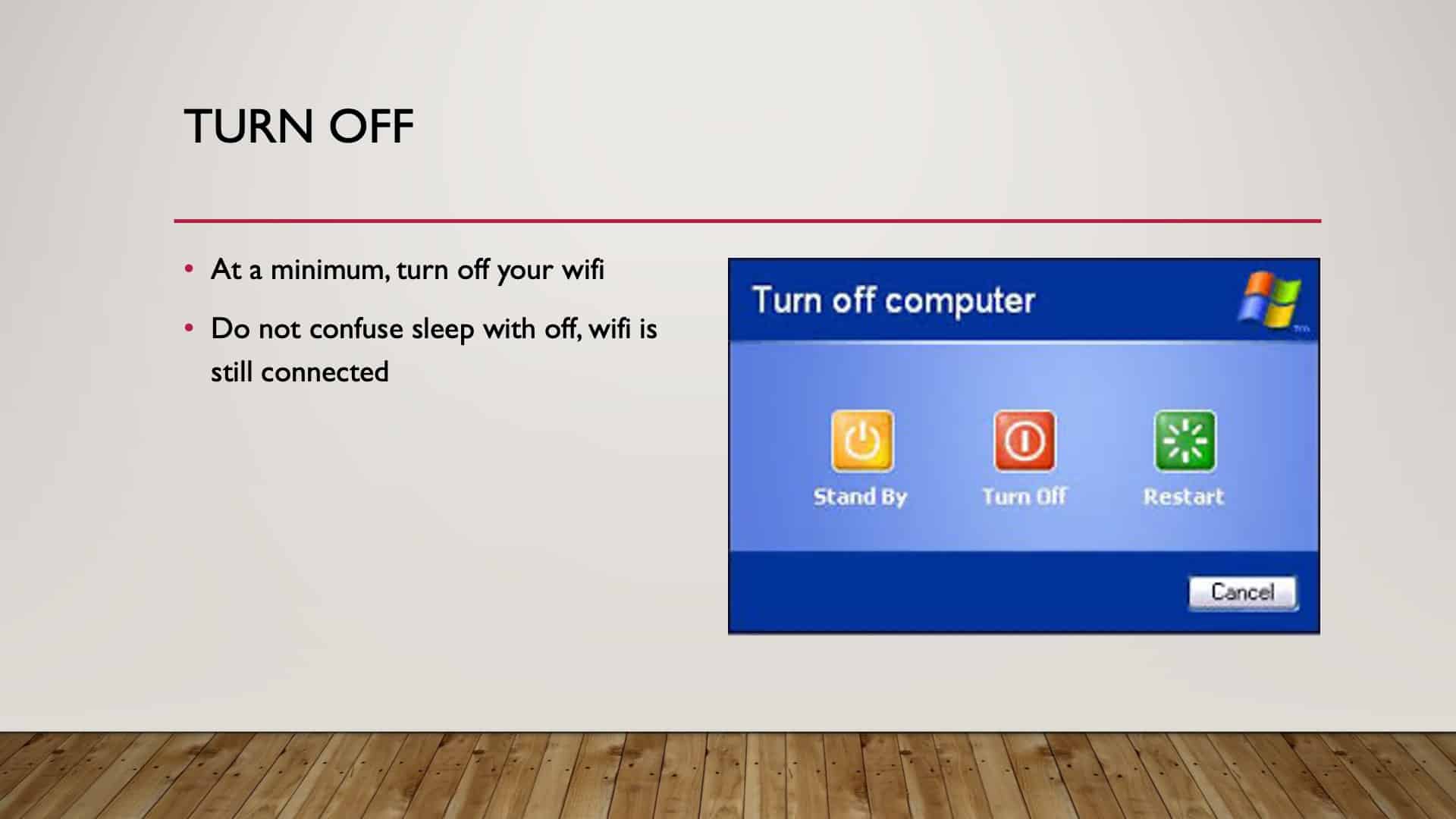
Another step to take is turn it off. The best form of defense is turning off. No power, no access. It’s that simple. We had a great example in one of our live workshops, where we talked about ransomware, and we’ll get into ransomware in a little bit.
But the participant in the workshop had said, “I’ve been infected by ransomware twice. The first time I saw this thing installing and I was interested in watching what was happening, and the next thing, boom, I’m locked out of my computer, and I’m subject to ransomware.”
“The second time, because I was experienced, I saw this thing installing, and it looked so familiar, I quickly unplugged my computer from the wall. And when I plugged it back in, it was gone, and there was no ransomware.”
So it’s all power-driven. It comes through power; it comes through connection. No power, no problem. If you don’t need to be on your computer, switch it off. Save yourself some issues, right? And don’t confuse sleep with off because it still has access to WiFi. You still are connected, even though you are in sleep mode.
Encryption

As we saw through the password exercise, taking something that’s plaintext, putting it into something that’s jibber-jabber that makes no sense, that’s the simplest way to think about encryption.
Just as I sit here in front of Paul’s computer, this is Paul’s computer, and he has a lot of sensitive data here. If he switches it off and he’s enabled the Mac FileVault, it automatically encrypts all of the data on his hard drive the minute he switches it off.
So if someone steals it and doesn’t know his password or how to unlock that FileVault, it’s meaningless to them. It’s just complete jibber-jabber.
Use Your Tools
We have these free services. BitLocker on Windows, FileVault on Mac, just switch them on. It encrypts everything.
And encryption is crucial. Encryption doesn’t mean just on hard drives; that means as I send an email out into the big wide internet world, I can have it encrypted, I can have it unencrypted. If somebody intercepts that transaction between me and who I’m sending that to, and it’s not encrypted, there’s plaintext that can read it. If it’s encrypted, they’re going to have to figure out how to decrypt it, and then it becomes very complicated.
So encryption is important in a lot of different ways. On our hard drives, in our emails, in our correspondence. Encryption is key. Even as we go into storage in the cloud, everything now is cloud-based, is it encrypted on the way to the cloud? Is it encrypted in the cloud? And is it encrypted on the way back back to my computer or to my device?
The Cloud

Again, just in talking about the cloud, storage is important. We’re going to a cloud-based world, as it exists, becoming way more common.
Everything’s in the cloud. So how is it being stored? Just be aware, ask the question, is it encrypted? Is it encrypted on the way there, on the way back? Very important. We want our stuff encrypted.
If you have information that you could not be bothered that people see, don’t worry about encryption, but if you don’t want people to see it, encrypt it.
Public WiFi

Public WiFi is a big red flag because it’s not necessarily secure, and your information that you make available through public WiFi can be sold. Right? FCC chairman voted that that’s okay, let’s sell it, but he likes his privacy, right?
I say that with tongue in cheek, but what’s good for the goose has to be good for the gander. So if you have to get onto public WiFi for whatever reason, because you want to see where you want to go to lunch, then, by all means, do it, but do not get onto public WiFi and start putting in passwords and banking information.
Instead, set your phone up as a hotspot and then connect your device to your WiFi instead of logging into public WiFi in a public setting and doing sensitive banking. It’s a huge risk. Okay?
I know it’s a lot, but remember, there’s the resource guide that’ll bring it all back together as we got through this quite quickly.
Ransomware
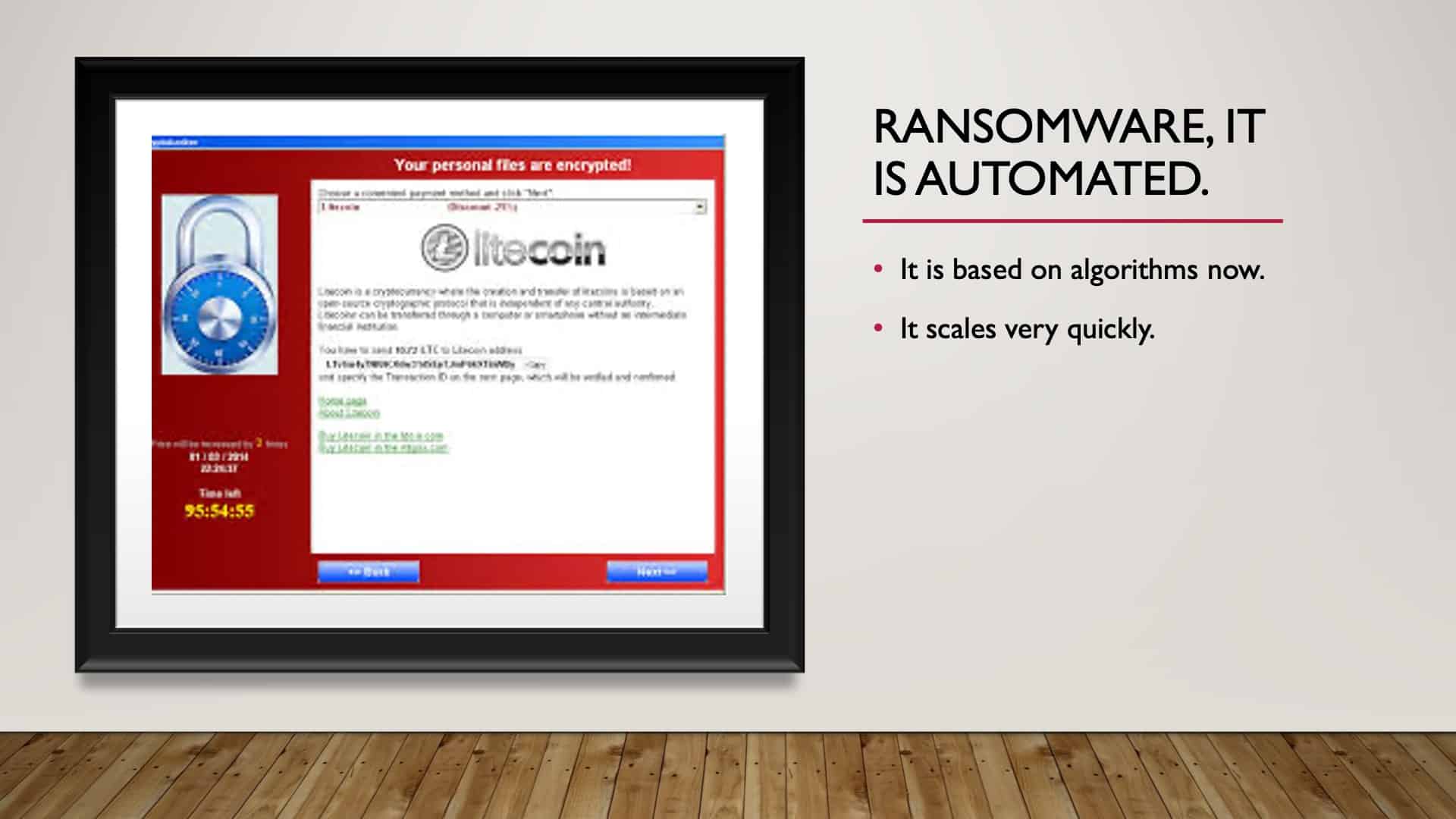
Ransomware is automated, and it’s a big deal. It’s a big, big problem. Now there’s a whole new twist to ransomware. Not only are criminals locking your information, but in the process of infecting your device or network, they’re stealing data and holding the data as ransom. So the best way to avoid ransomware is cyber hygiene.
Cyber hygiene requires us to be so aware and so careful about what we click on, and it’s getting more difficult to identify malicious links or emails. So ransomware, it’s also kind of funny and not funny, but criminals can infect your computer with ransomware.
What ransomware ultimately means is they are encrypting your device with an encryption key that they have. And the only way that you can unencrypt or decrypt your device is pay them for the key. And then, in theory, you pay them, they send the key, they give you back your data.
How Can You Avoid Ransomware?
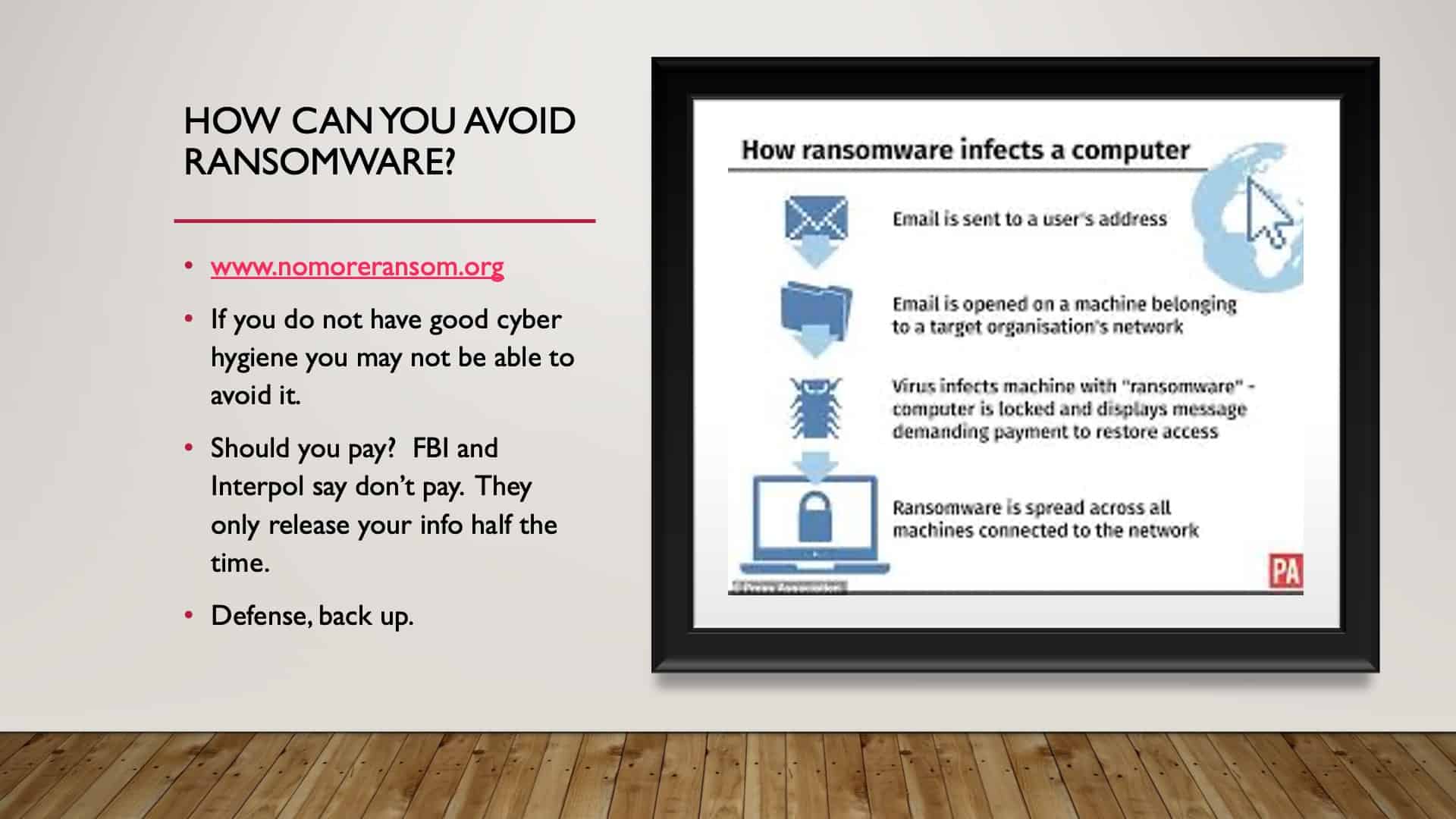
Marc basically says, “Don’t pay because 50% of the time you don’t get your data back anyway.” Right? So we’ll talk about how to protect yourself from ransomware best. But there’s a resource called nomoreransomware.org which can help maybe. And it can be pretty complicated to try to figure out how to decrypt.
The example that I gave earlier with the guy in the workshop with us who had ransomware impact him, the first time he got infected, he took his laptop to Best Buy. The Best Buy geeks figured it out, got him decrypted, and got his information back. So that’s great. Now that’s fortunate that it was maybe a weak version of ransomware.
If you get hit with a pretty strong one, it could be impossible to decrypt, and you lose your data. So the best form of defense is a backup. Because if you lose your data to ransomware and you have a very current backup, you can wipe your own, bring your back up back online, and you pick up where you left off.
How Do You Get Ransomware?
Typically the way that we get ransomware is listed here. How ransomware infects a computer; somebody sends an email, we click, we open the email. We click on the link virus and fix the machine, ransomware in the computer is locked, they demand payment, we pay, we’re supposed to get our data back.
What’s funny is the ransomware criminals want Bitcoin; it’s what they want. Wherever in the world. And if you don’t know how to buy a Bitcoin, there are tutorials embedded in their ransomware to teach you how to buy Bitcoin to pay them their ransom.
Backup Your Data

This is key. If we have a fresh backup, we have a backup plan. We can have an external hard drive backup that we can plugin, keep it. And keep that encrypted because that can get stolen too. And we can have a cloud-based backup.
Again, talking about encryption, as we back up to the cloud, is it encrypted on the way up? Is it encrypted in the cloud? Is it encrypted coming back down? If you have a fresh backup, you’ll have no problem.
Access Denied

Ways people can access your data, again, bring that image up because it’s the most common, most consistent. We go to the airport and take a USB, and we plug it in because we think we’re getting power, but a USB is most definitely a transfer of both power and data. So behind the scenes at the airport, we plug into a USB port; who’s to say that that thing isn’t stealing data but just be aware of that.
Have passwords on your cell phones, have two-factor authentication where you can, have firewalls turned on at home now as we’ve got a smart home, so we can have firewall defenses in our house, which is essential. And then USB ports; protect them.
PortaPow
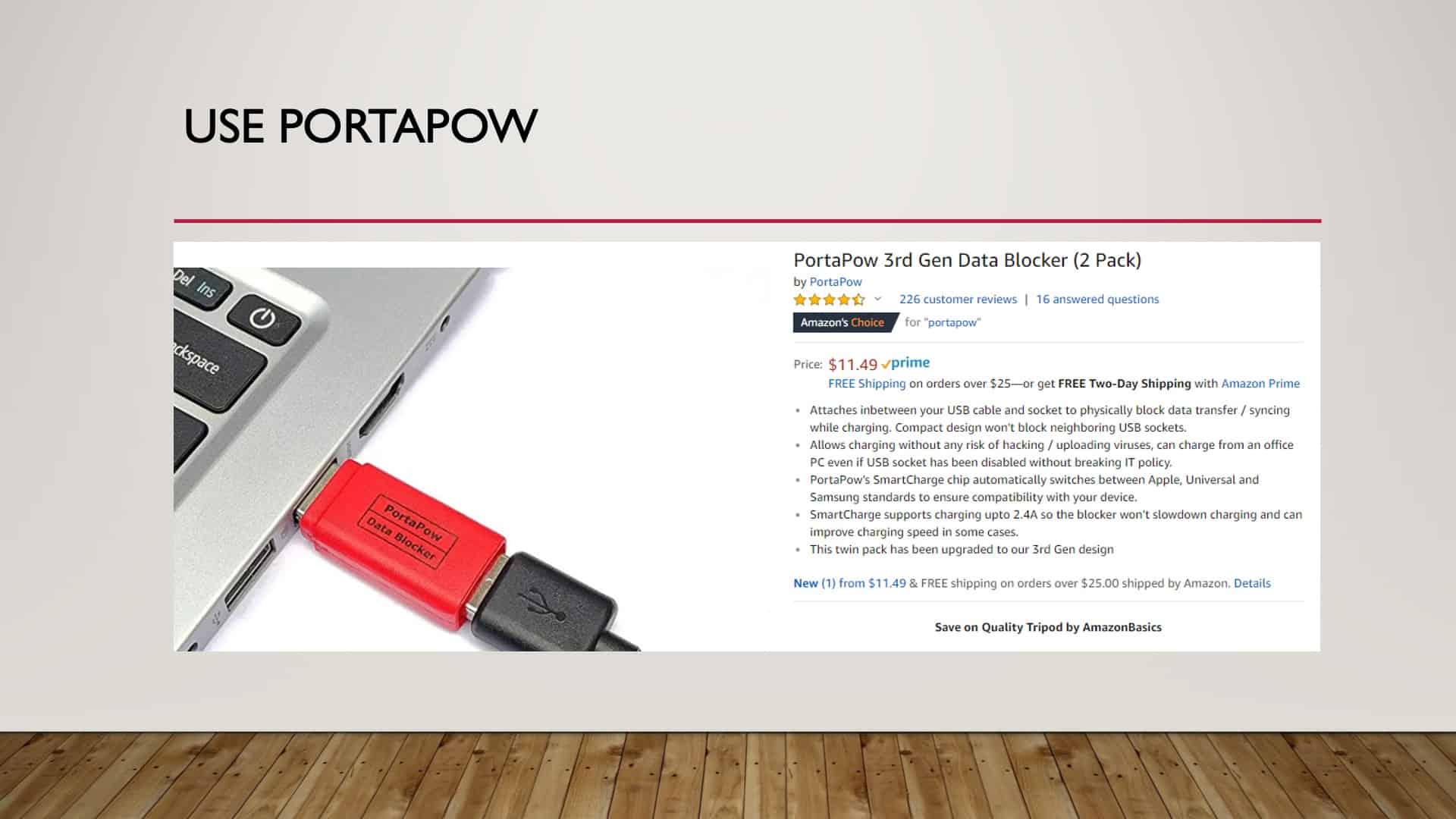
Here’s an example of a device from Amazon. I have one. It’s called a Portapow data blocker. This is a barrier between your power cable and the USB port. So all that it allows for is the transfer of power to your device.
So it charges, but it doesn’t allow data to go back and forth. If you travel a lot and plugin into public places, I would encourage you to get one of these.
Stop, Think, Click, and Hover

I think there’s one word that we’ll address, which is hover. In some instances, I don’t know if it’s true, a lot of times for Microsoft word if we hover over a link, right?
The New Normal, Hover
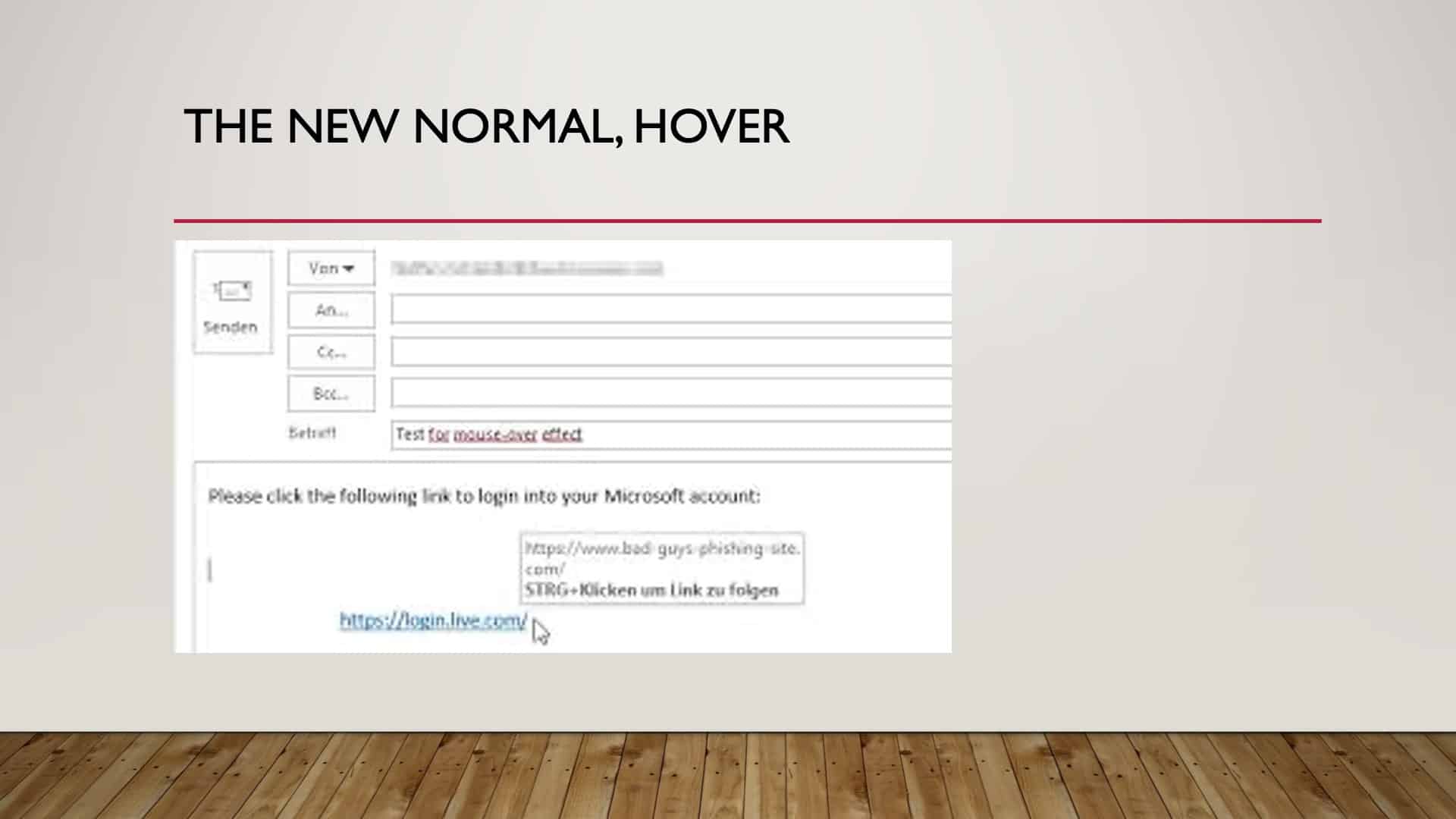
If we hover over it as you see here, we hover over, and so it’s a little bit blurry, but if we hover in the link, it says, login.live.com and we hover over it, it’ll give us the actual source of that link. And we can then see that this claims to be coming from Microsoft, yet the link has no reference to Microsoft whatsoever.
So if we hover over things sometimes, it’ll give us a clue, and we don’t click on them. If we clicked on that without thinking, that is malicious, and it’s going to install something unhealthy on our computer. So going back to this, stop, think, hover, click, just say that over and over until it’s just second nature. Stop, think, hover, click.
Cameras

Ooh, cameras they’re watching. They are watching. There are some horrible stories in Marc’s book about how people were hacked. The sextortion, which is a terrifying phrase in itself.
So if you’re unaware that someone’s watching you and recording you, and then the next thing they’re blackmailing you because they have images that you don’t want the world to see, it happens. So how do you protect yourself?
Something as simple as sticky paper, the sticky notes, tear it off, stick it over your camera, is one way.
Two, you can get a slider, which I’ve got a special surprise coming up for everybody in a minute. But keep your cameras protected. Change the passwords. When you buy a camera that connects to your WiFi, the password is something simple, like admin, that somebody can hack into. Change that password, protect yourself.
Recap
So we’ve come to the end, our recap.
These are the steps. They’re listed in the protocol and resource guide available at the top of the page.
We have to update, make sure passwords are strong, long, safe, and protect your WiFi routers. Be very careful what you download, and get out of the administrator account. Turn off your devices when you don’t need them, and make sure everything’s encrypted and then make sure you have a backup.
If we can follow these steps, you can eliminate 85% of your risk. You put yourself way up there in that tree, and the criminals aren’t interested in chasing you anymore. They like the low-hanging fruit. You’re not going to be low-hanging fruit anymore.

For those of you who participated and you’re not present with us today, I am very sorry that we cannot hand you one of these gifts in person, but you’re more than welcome to stop by the office in Lenexa. Paula will have them upfront. We’re happy to give you a webcam slider. So that has sticky tape on it, it attaches to your screen, and you can slide that slider to open your camera and close your camera so that you have privacy at your leisure. Very important.
The Guided Retirement Show Episode
So if you have any additional questions, Dean and I have done a podcast on this subject; we had a lot of fun doing it. I mean, I kid you not. It was a blast just recording it with Dean.
So if you have additional interest in the subject matter, please go and listen to the podcast. I’m sure you’ll find it just as enjoyable as we did making it.
Thanks for Joining Me
So for everybody that attended, thank you so much. You can find the resource guide and the update protocol in the resources section at the top of this article. Thank you, everybody, for attending.
Schedule Complimentary Consultation
Click below to get started. We can meet in-person, by virtual meeting, or by phone. Then it’s just two simple steps to schedule a time for your Complimentary Consultation.
Investment advisory services offered through Modern Wealth Management, LLC, an SEC Registered Investment Adviser.
The views expressed represent the opinion of Modern Wealth Management an SEC Registered Investment Adviser. Information provided is for illustrative purposes only and does not constitute investment, tax, or legal advice. Modern Wealth Management does not accept any liability for the use of the information discussed. Consult with a qualified financial, legal, or tax professional prior to taking any action.